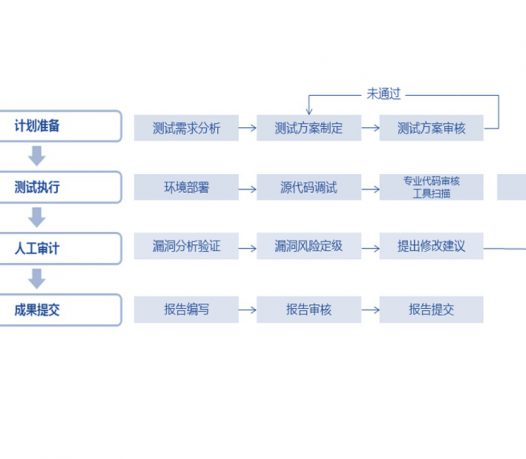
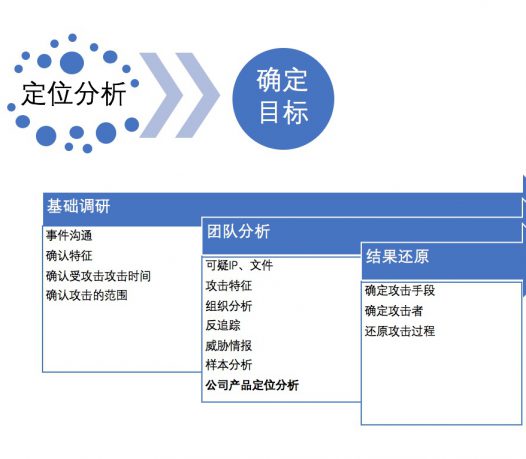
We have an experienced security team that provides low-cost products and high-quality services for you.
The company has brought together offensive and defensive teams and R&D teams with over 10 years of experience in the information security industry. Many of our technical staff have obtained relevant industry security certifications, such as CISP, CISSP, and CISA.